Setting up Elastic Defend: this is the EDR (Endpint detection and response) and generate some telemetry. ES > management > integrations > Elastic Defend Add elastic defend Select existing host […]
Investigating the things to look for in a brute force attack Go to ES > Security > alerts We look to investigate the following when we investigate an Alert and […]
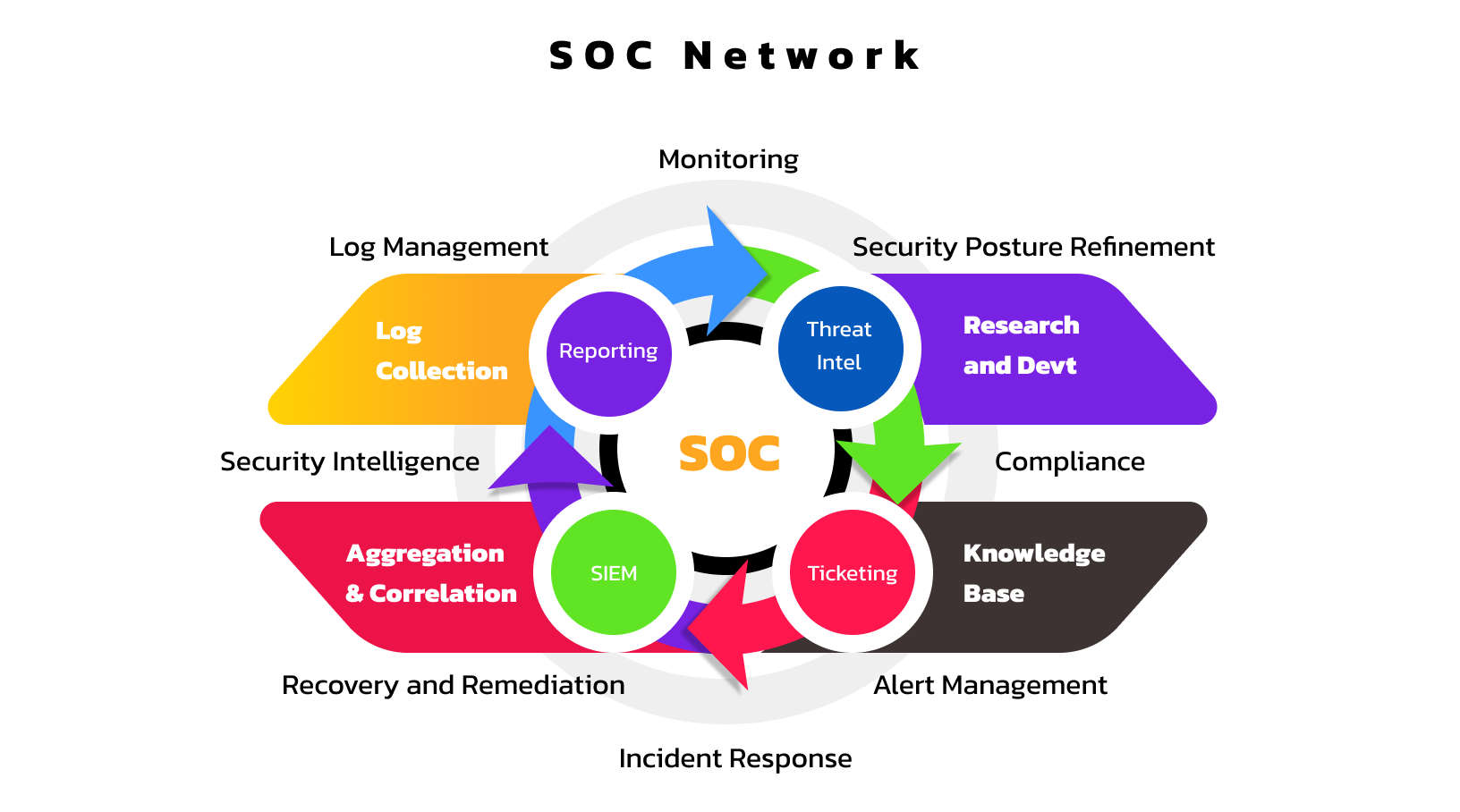
Helps keep track of the task at hand, provide an audit trail and accountability. From a SOC perspective, a ticketing system is essential in fulfilling the AAA triad (AAA Framework) […]
Setup a Kali Linux on your local system (Not cloud). This will be our attack machine for the Command and Control Operation. Mythic server requires a minimum of 2 vCPUs […]
Events generated for our Linux Agent is seen below, we have a total of 387 events. In creating our dashboards, we will be focusing on the following fields: We click […]
E – ElasticSearch : (Store, Search, Analyze)This solution helps you securely take data from any source, in any format, search, analyze and visualize it in real time. In our case, […]
This challenge in aimed at gaining SOC (Security Operations Centre) analysis skills. I will be exploring different aspects of SOC operations and analysis –setting up the ELK (Elasticsearch, Logstash and […]