Next, we Setup a new Linux SSH Server as a Test machine for monitoring Brute Force attacks:
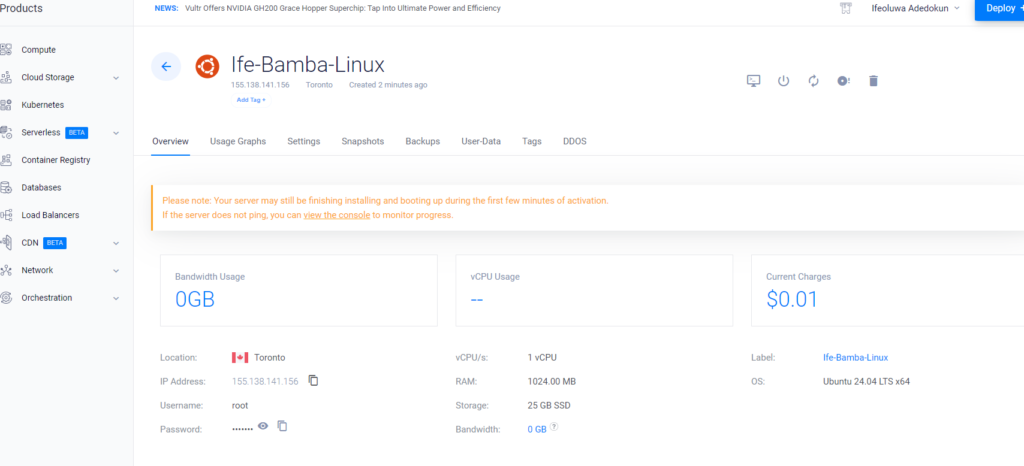
SSH into the server and update your linux:
> apt-get update && apt-get upgrade -y
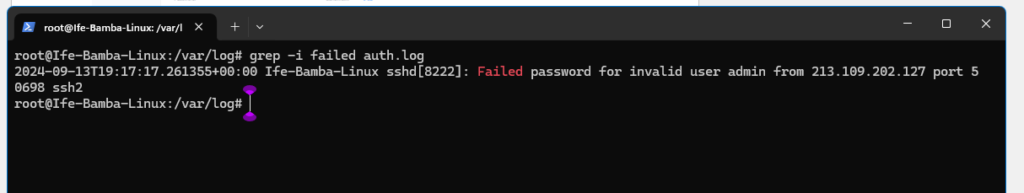
> browse to the /var/log directory, note the auth.log file which we will use to monitor login attempts
We leave our Linux Server ON for some time and then we view the auth.log command again to discover login attempts from various sources on the internet:
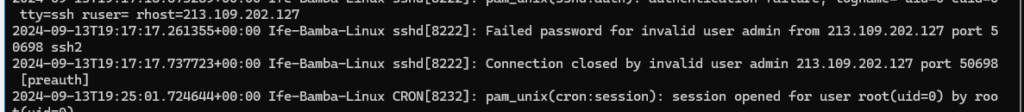
- grep -i failed /var/log/auth.log
- This command searches for the “failed” string in our /var/log/auth.log file while ignoring case sensitivity (-i option)
Objective 12:
Installing Elastic Agent on SSH Linux Server
Go to Elasticsearch > management > Fleet >Agent Policies > Create Agent Policy > create
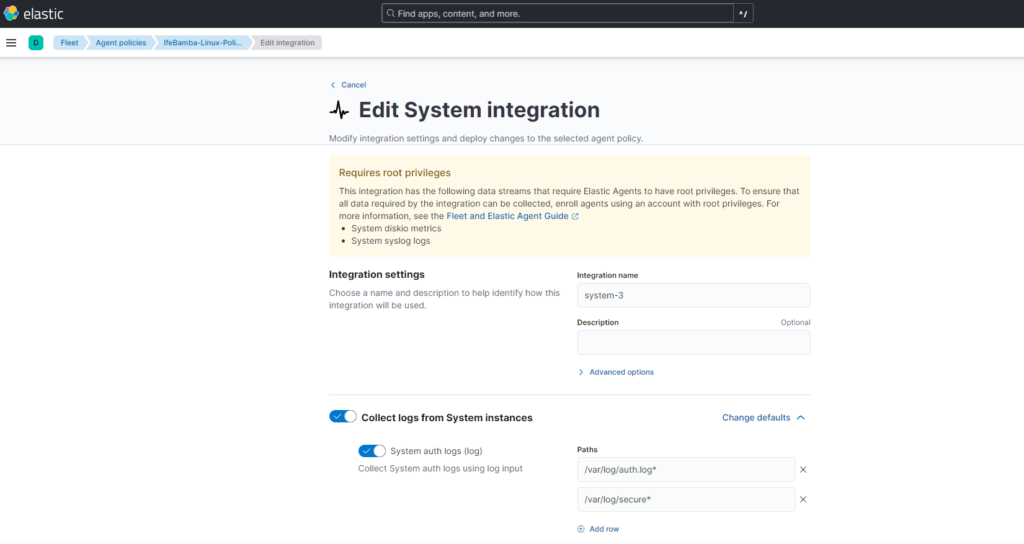
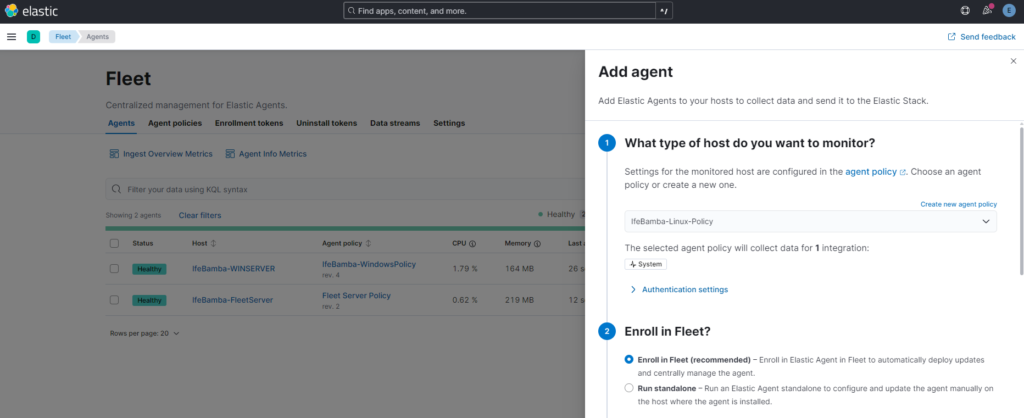
Go to Elasticsearch > management > Fleet >Agent > Add Agent
Select the Linux Policy you just created
To install on Linux Host, copy the Linux command:
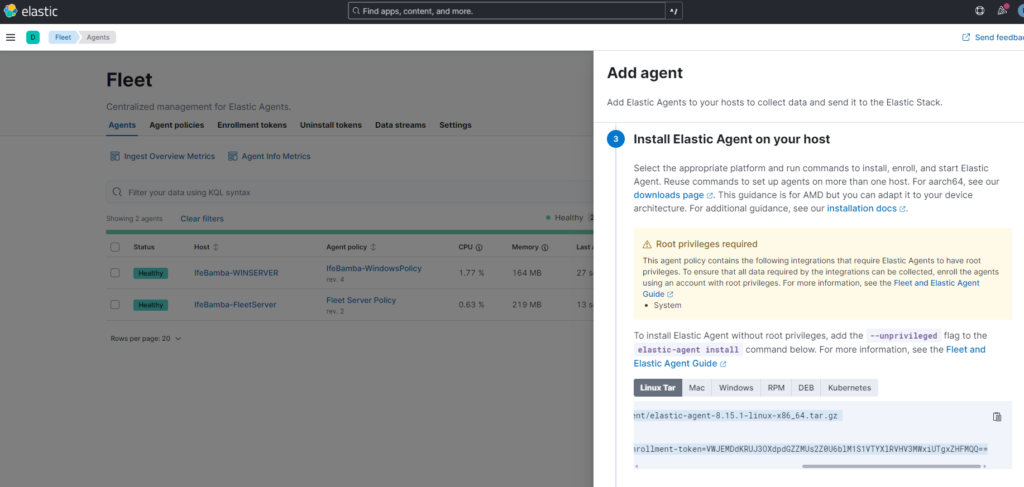
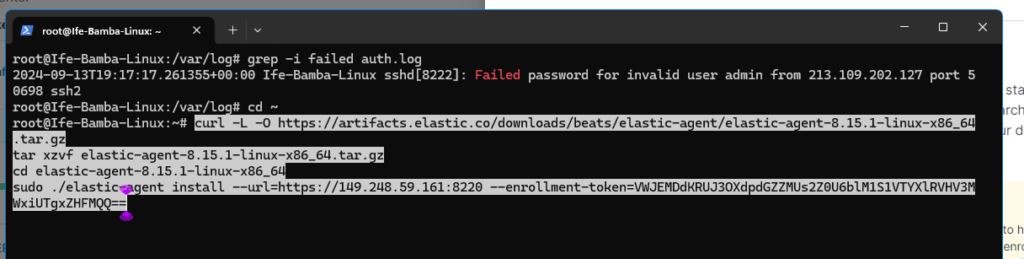
Edit the command and and the “ –insecure” flag to allow agent installation without the need for a signed certificate.
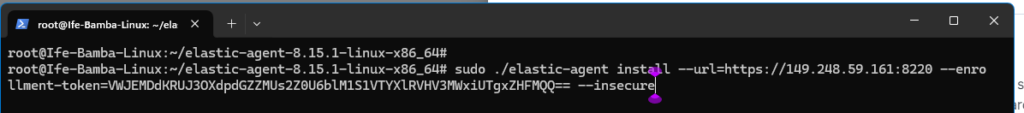
Install complete:
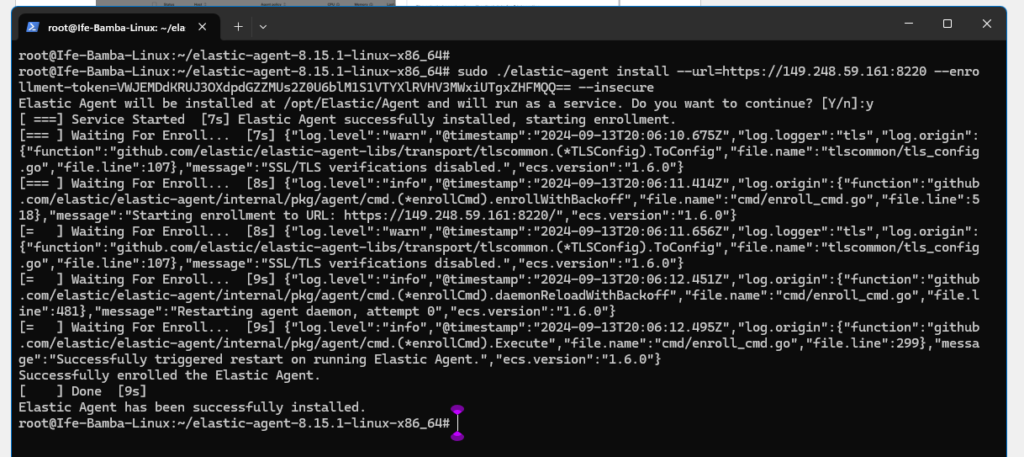
Agent Enrollment confirmed:
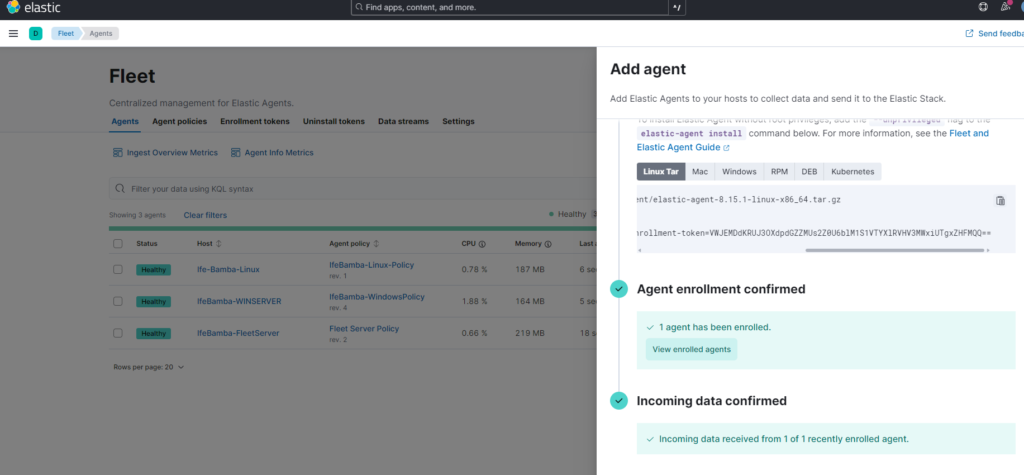
ElasticSearch > Analytics > Discover
we see that our Linux Agent is registered in ElasticSearch for logs
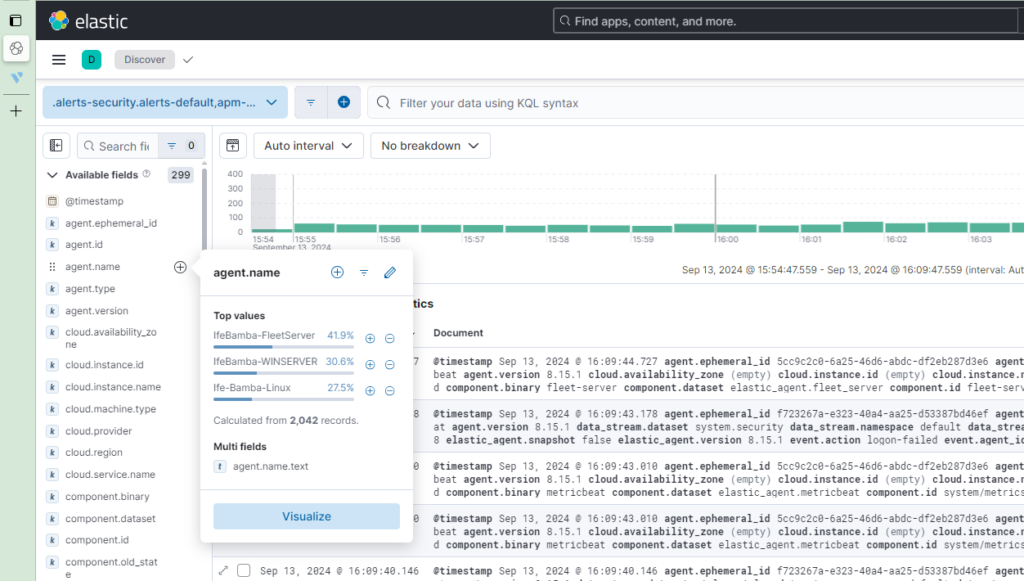
Lets check our /var/log/auth.log file on the Linux server again with our grep command:
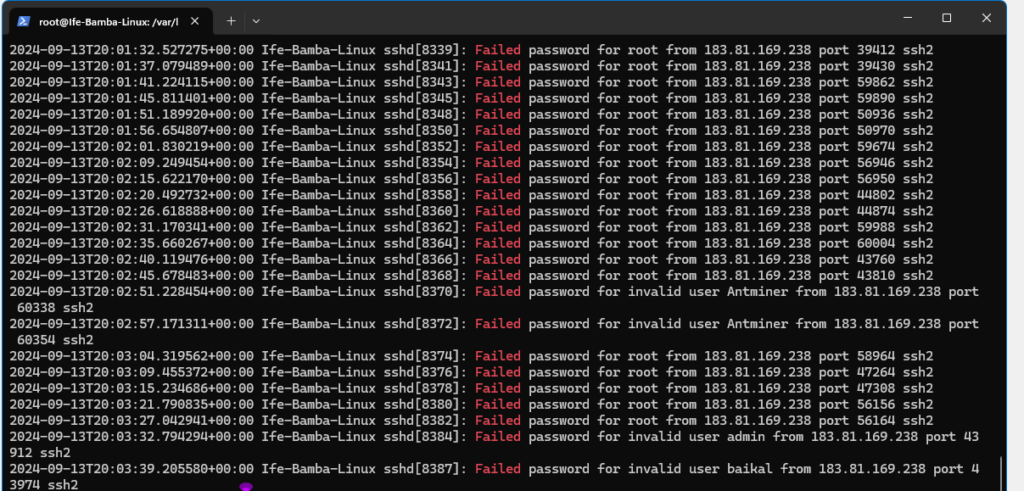
We see more failed login attempts!!
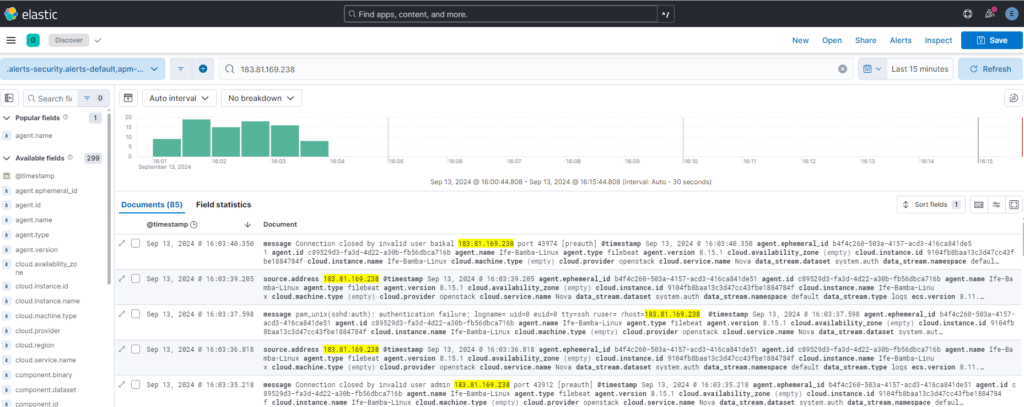
Lets search the culprit IP : 183.81.169.238 by using it as a search query inside Elasticsearch:
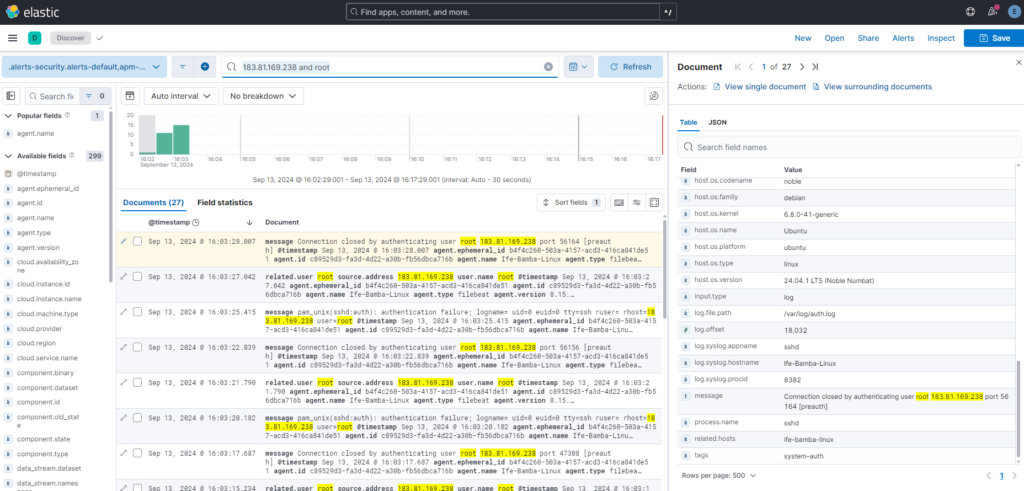
Lets see how many times this IP tried to login using the root account unto our server : Search using the “183.81.169.238 and root” query:
Understanding brute force attacks
A brute force attack is when an attacker tries to use any password combination in a bid to compromize systems.
Types of Brute Force Attacks (BFA):
1. Brute Force: trying any possible combination using tryal and error; done in an automated fashion
2. Dictionary attack: similar to BFA but uses a dictionary list thet contains common words, phrases and/or password found in credential dumps.
3. Credential Stuffing: The attacker uses credential dumps to take advantage of re-used passwords and tries every combination including both usernames and passwords.
How to prevent:
1. Use long passwords and passphrases (make it more complex) – use a password manager
2. Use MFA
3. Vigilance and being alert to prevent social engineering attacks
Common BFA tools
1. Hydra
2. Hashcat
3. Jack The Ripper