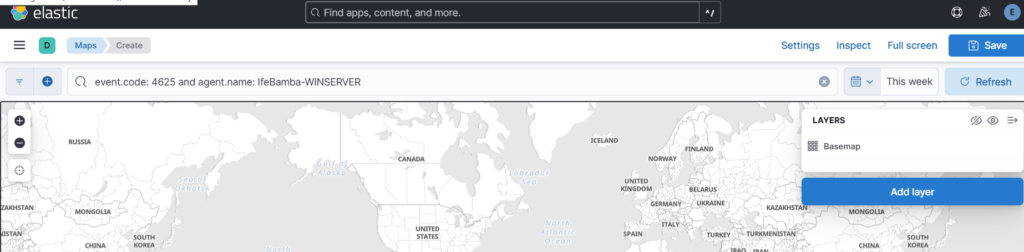
Elasticsearch > Analytics > Maps … the you can compose your query:
event.code: 4625 and agent.name: IfeBamba-WINSERVER
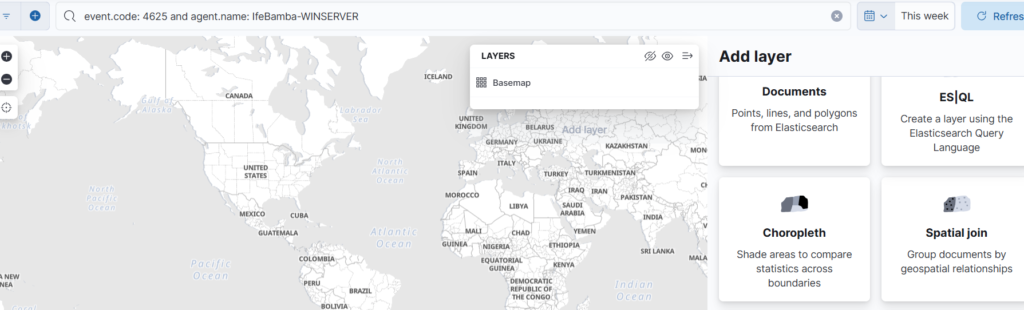
Add Layer > Select Choropeth:
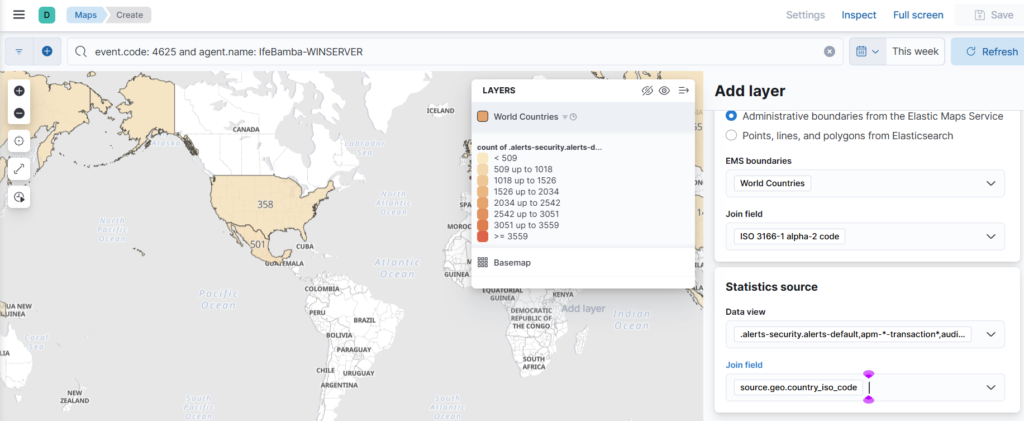
Use the Add layer options as seen in the screenshot below: EMS boundaries, Join field, data view and join field
Save the Map and add to the Authentication Activity dashboard created earlier:
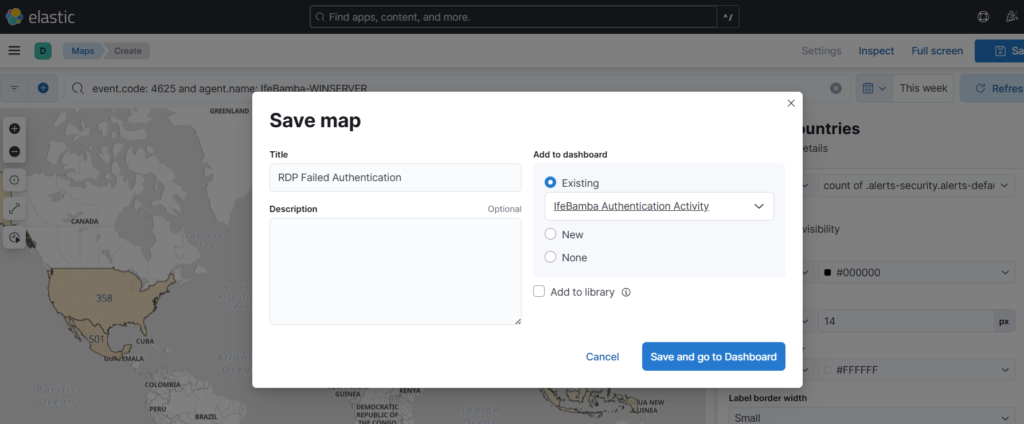
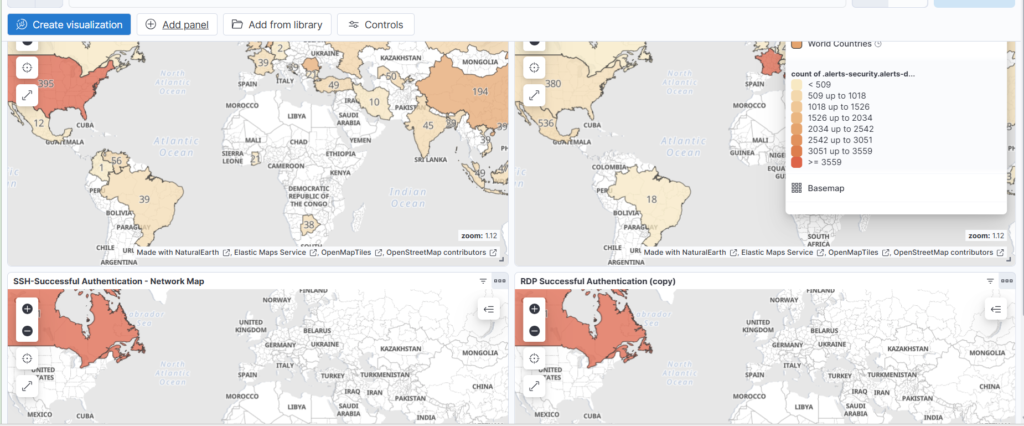
Dashboard showing failed SSH, Failed RDP, Successful SSH Maps:
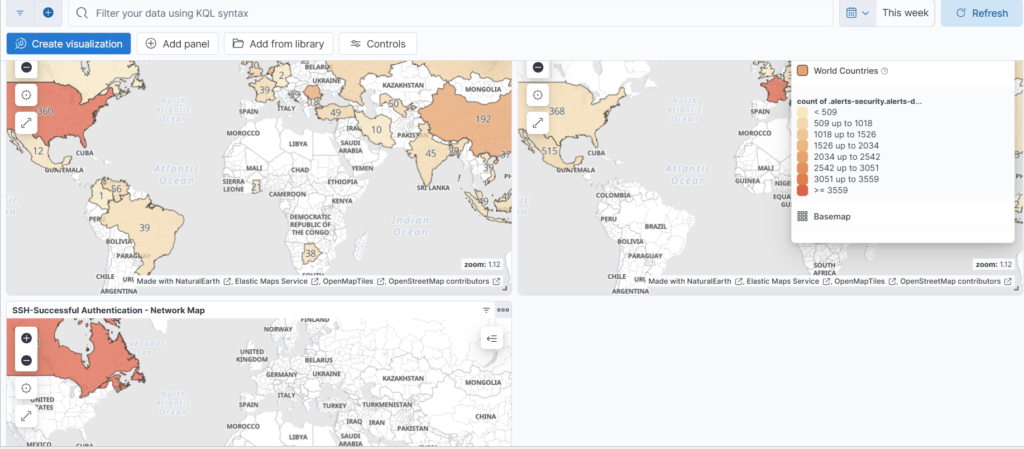
We want to add an additional map to our dashboard – A successful RDP login Map. First we determine the event ID for successful logins into windows: 4624.
Secondly, we know that services are allowed to authenticate with windows which will also generate the same ID: 4624. Take a look at this document on login IDs for windows:
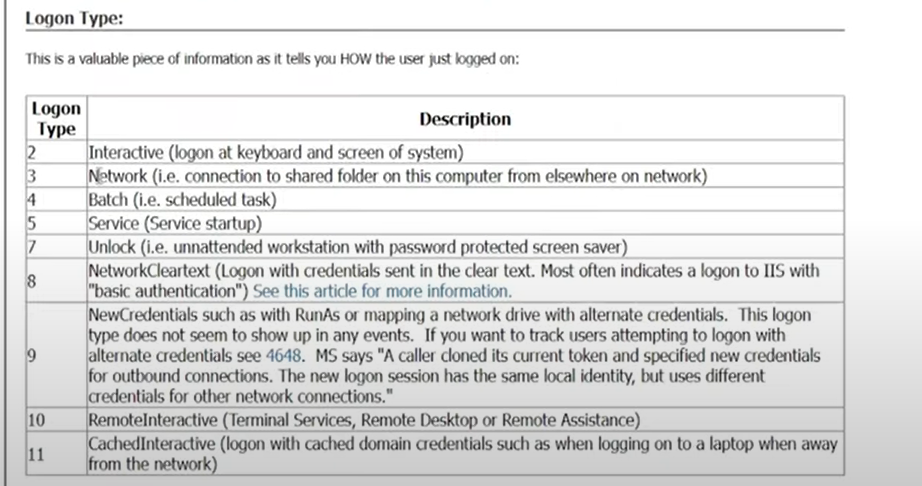
In this case, we are interested in login ID of 7 or 10. This is essential to avoid generating maps and dashboards with false positives of logins such as service logins (login ID 5). Hence we will use the event ID: 4624 AND login ID’s 5 and 10 to generate our query for RDP successful logins.
Note the highlighed winlog.event_data.LoginType field above. We have to combine this with our map query to be able to generate the accurate map (successful RDP logins) for our dashboard.
How to find this field?
ES > Analytics > Discover
– Search for the “event.code: 4624”
– Expand any of the log results
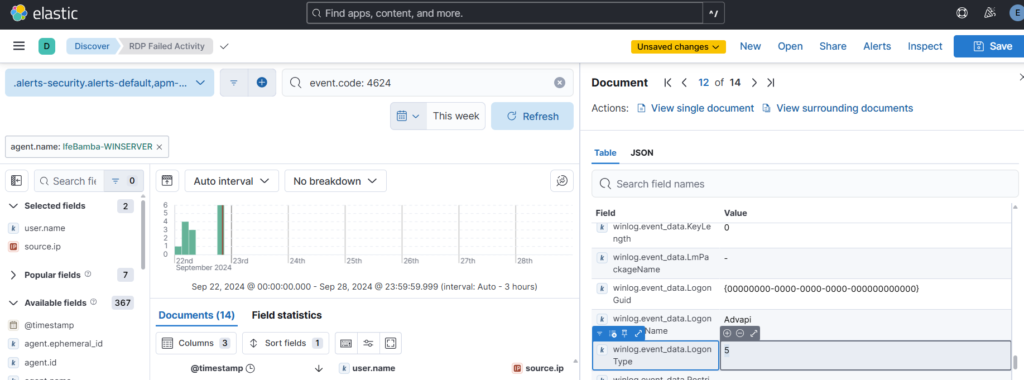
– Look out for the highlighted Message column with the login information as in the screenshot below: we see Logon Type: 5
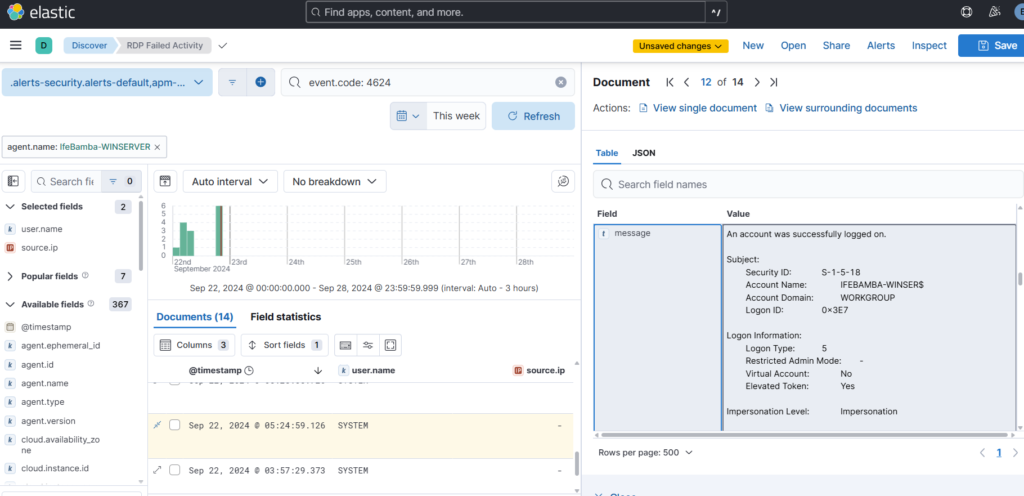
We scroll down the log details and see the exact field that shows this logon type: winlog.event_data.logonType. This is what we will use for our map query.
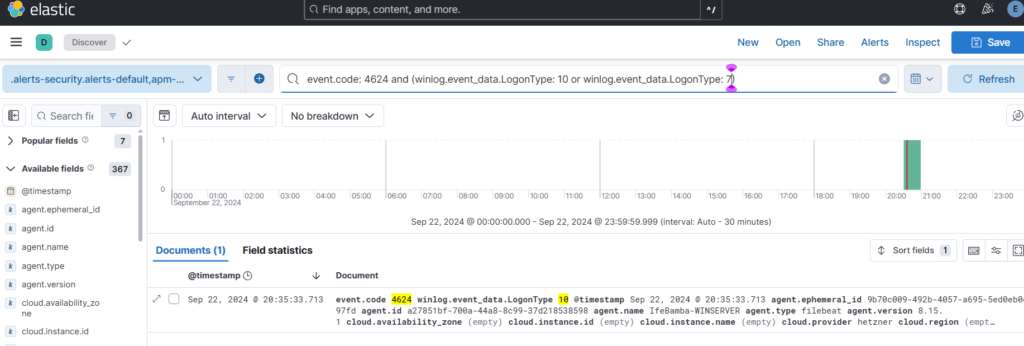
Map Query:
“event.code: 4624 and (winlog.event_data.LogonType: 10 or winlog.event_data.LogonType: 7)”
ES > analytics > discover > paste in query
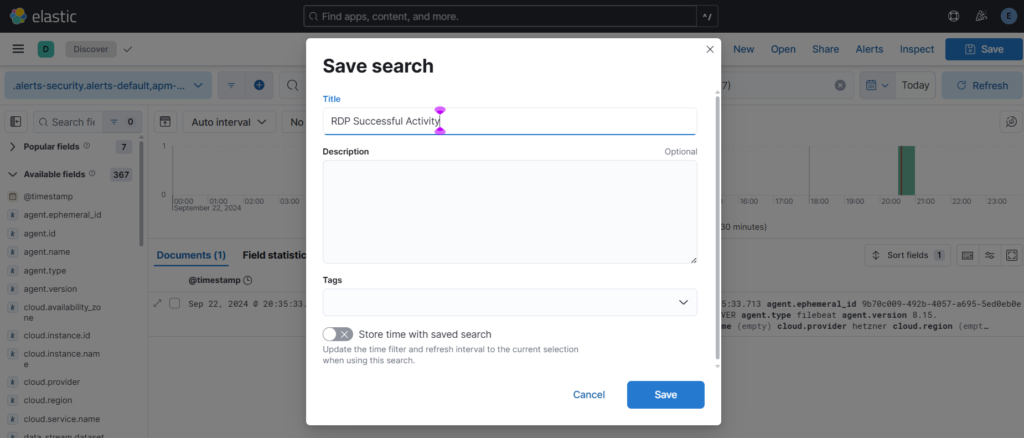
Save the search:
ES > Analytics > Dashboards. We duplicate the RDP Map created earlier and edit with the new name and query as below:
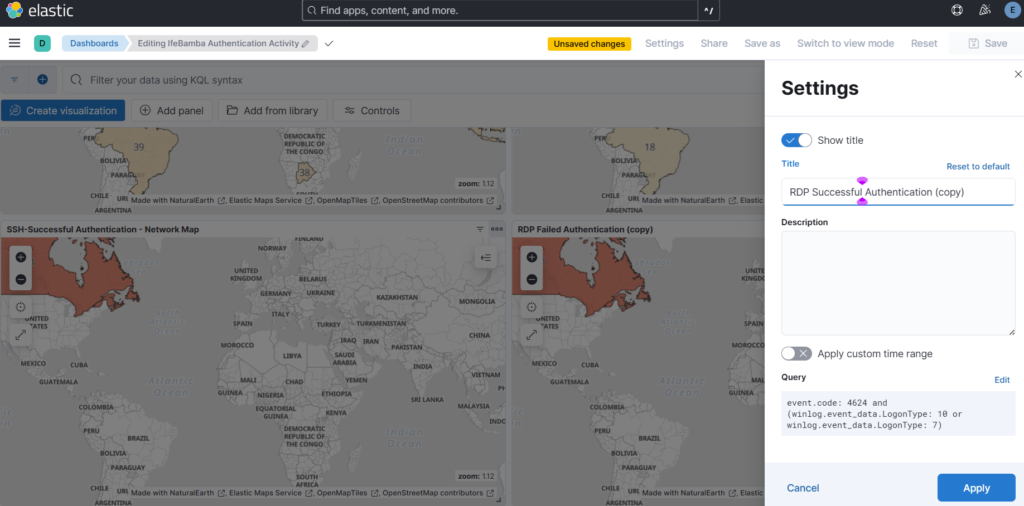
Dashboard:
Creating Visualizations :
Click on Create Visualization and paste the query :
system.auth.ssh.event: * and agent.name: Ife-Bamba-Linux and system.auth.ssh.event: Failed
Drag fields from the left sidebar into the center window: source.ip and timestamp fields are dropped in:
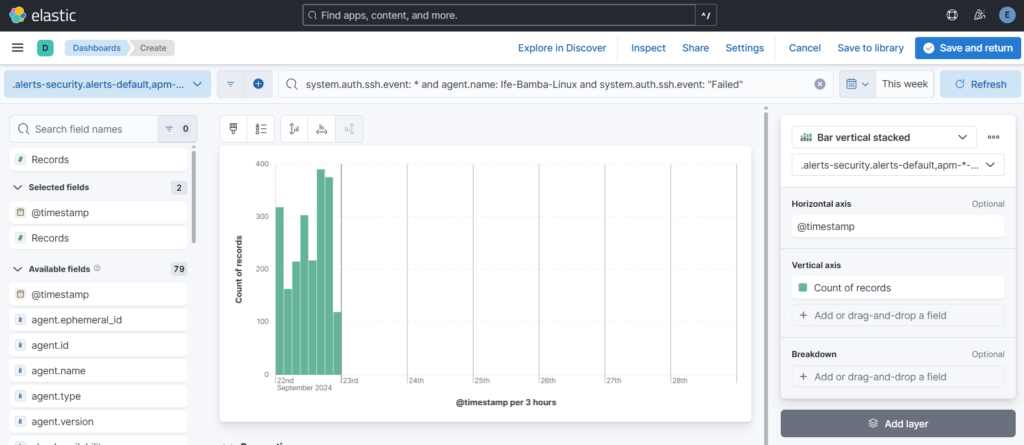
timestamp field added in
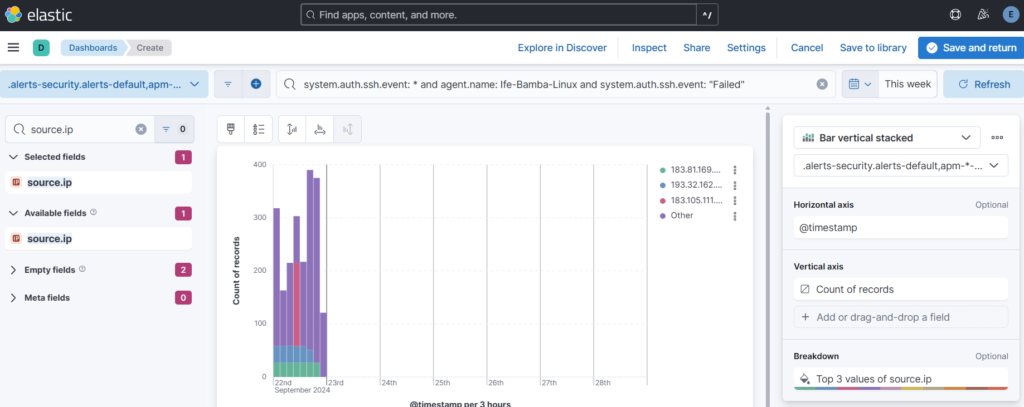
source.ip field added in
Lets change the visualization type to table:
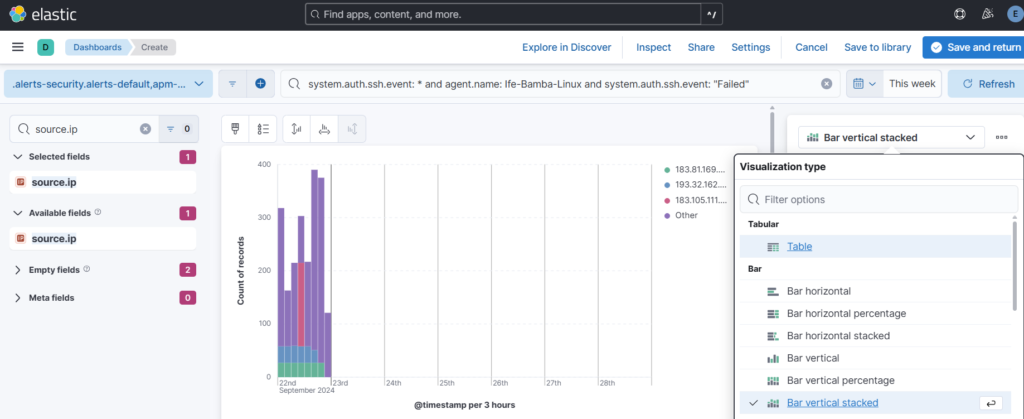
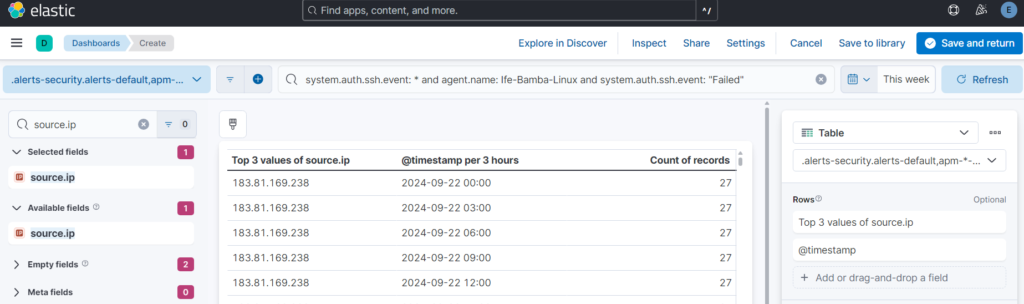
We can add more fields and remove some: remove timestamp, add user.name and source.geo.country_name
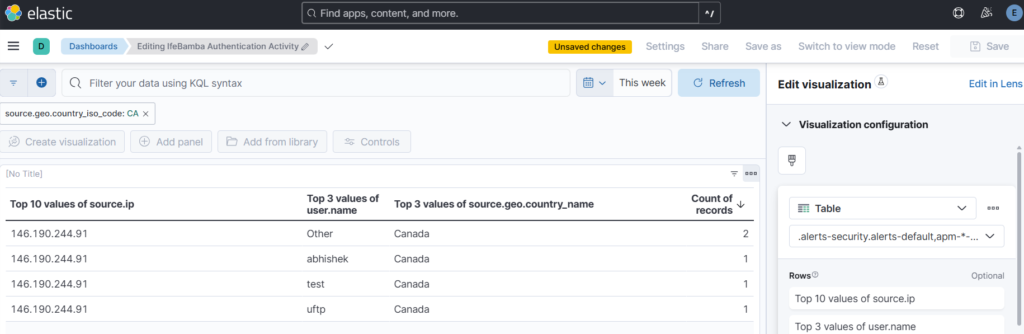
You can play around with the rows in the visualization, sort by ascending etc
Click on Edit in Lens > Save and Return. The table wil be added to the dashboard.
SSH tables added to the dashboard:
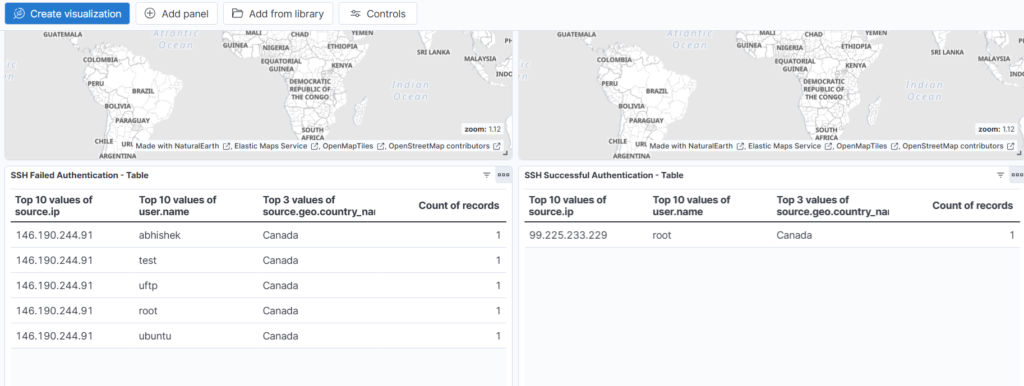
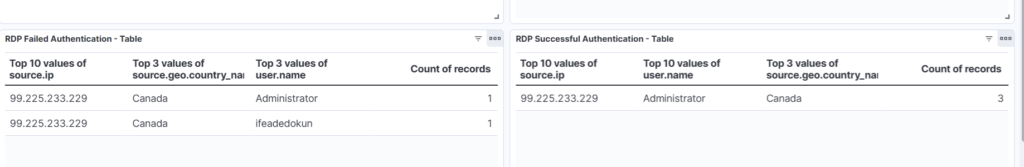
Let create tables for RDP authentications: We simply duplicate the SSH table visualizations and edit the queries:
RDP Failed Query:
event.code: 4625 and agent.name: IfeBamba-WINSERVER and user.name: Administrator
RDP Successful Query:
event.code: 4624 and (winlog.event_data.LogonType: 10 or winlog.event_data.LogonType: 7)